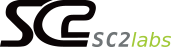PCI Software Security Framework (SSF) is a collection of two different and independent programs. The requirements, validation criteria, and SSC listing are divided into two standards - developed to secure the design and development of payment software.
The SSF currently comprises two separate standards:
The Secure Software Lifecycle Program (SSL) outlines the requirements and associated test procedures for software vendors to validate how they can properly manage the security of payment software throughout the entire software life-cycle. Secure SLC is applied to software vendors that develop software for the payments industry.
The Secure Software Standard (SSS or 3S) defines a set of security requirements and procedures to adequately protecting and securing the integrity and confidentiality of payment transactions and data.
Both standards will result in a listing on PCI SSC website - one of the two dedicated links. PCI SSC will list the company, the products developed under these processes, and what kind of product categories the vendor develops. The PCI Secure Software assessment will result in a list of the specific products that were validated.
SC2labs provides PCI SSF and PCI SSS validation services
as a qualified PCI SSA and PCI SLCA Assessor
certified by the PCI Security Standards Council.
The Secure Software Standard is applied to software products involved in or directly supporting or facilitating payment transactions that store, process, or transmit clear-text account data that is sold, distributed, or licensed to third parties.
Secure software core requirements:
Applicable to all software being certified to Secure Software Standard
Module A:
Applicable to software that processes clear cardholder data
Module B:
Designed and applicable to software that runs on PCI-PTS certified payment terminals
Module C:
Applicable to software with web-based interfaces
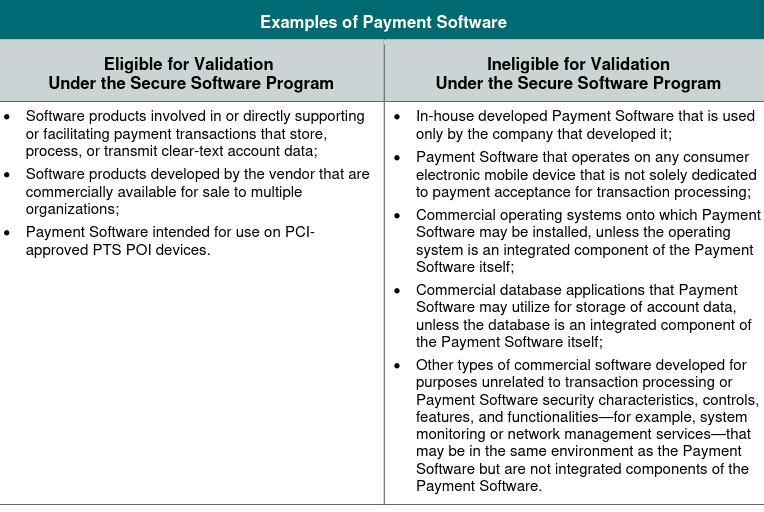
PCI SSF is an improved version of the PA DSS Standard by addressing recent advancements in payment technologies, platforms, and software development practices.
It is a payment security standard that includes elements of PA DSS, however replaces some topic with additional outcome-focused requirements that support a broader range of payment software types, technologies, and development methodologies.
Payment card organizations already introduced PCI SSF into their programs.
From https://mastercard.com/sdp:
Third party-provided payment applications and software
Mastercard requires all merchants and service providers that use third party-provided payment applications or payment software to validate that each payment application or payment software used is listed on the PCI Security Standards Council (SSC) website as compliant with either the PCI Payment Application Data Security Standard (PA-DSS) or the PCI Secure Software Standard, as applicable. Mastercard recommends that merchants use a Qualified Integrator & Reseller (QIR) listed on the PCI SSC website to implement a PA-DSS-compliant payment application. It is also strongly recommended that merchants and service providers using third party-provided payment software ensure the payment software vendor complies with the PCI Secure Software Lifecycle Standard.
Secure Software Standard (SSS) and Secure Software Lifecycle (SLC) are both three years programs that focus on different aspects of software security validation.
While SLC validates the security controls and practices of the software design and development, the SSS reviews the overall effectiveness of the security of the software. Vendors may be validated for Secure Software Lifecycle and may be validated for a separate Secure Software Standard for payment software’s developed.
Secure SLC validation can simplify the process of maintaining the validation of your payment software when making changes. If you are SLC validated, you can make low-impact changes and submit the relevant documentation to the PCI SSC to update the software version listing, without paying fees. If you are not Secure SLC validated, the low impact changes must be reviewed by an assessor and relevant documents will need to be submitted to the PCI SSC.
The Secure Software Core Requirements are broken into four main security objectives:
1: Minimizing the Attack Surface:
Core Objectives 1: Critical Asset Identification;
Core Objectives 2: Secure Defaults;
Core Objectives 3: Sensitive Data Retention.
2: Software Protection Mechanisms:
Core Objectives 4: Critical Asset Protection;
Core Objectives 5: Authentication and Access Control;
Core Objectives 6: Sensitive Data Protection;
Core Objectives 7: Use of Cryptography.
3: Secure Software Operations:
Core Objectives 8: Activity Tracking;
Core Objectives 9: Attack Detection.
4: Secure Software Lifecycle Management
Core Objectives 10: Threat and Vulnerability Management;
Core Objectives 11: Secure Software Updates;
Core Objectives 12: Vendor Security Guidance.
Module A: Account Data Protection Requirements
Security requirements for software that stores, processes, or transmits account data.
A.1: Sensitive Authentication Data
A.2: Cardholder Data Protection
Module B: Terminal Software Requirements
Security requirements for software intended for deployment and execution on PCI-approved POI devices
B.1: Terminal Software Documentation
B.2: Terminal Software Design
B.3: Terminal Software Attack Mitigation
B.4: Terminal Software Security Testing
B.5: Terminal Software Implementation Guidance
Module C: Web Software Requirements
Additional security requirements for payment software intended for deployment and operation using internet-accessible clients and technologies.
C.1: Secure Software Components
C.2: Secure Authentication and Access Control
C.3: Secure Input Handling
C.4: Secure Communications.
The PCI Secure SLC Requirements are organized into four main sections:
Software Security Governance:
Core Objectives 1: Security Responsibility and Resources;
Core Objectives 2: Software Security Policy and Strategy.
Secure Software Engineering:
Core Objectives 3: Threat Identification and Mitigation;
Core Objectives 4: Vulnerability Detection and Mitigation.
Secure Software and Data Management:
Core Objectives 5: Change Management;
Core Objectives 6: Software Integrity Protection;
Core Objectives 7: Sensitive Data Protection.
Security Communications:
Core Objectives 8: Software Vendor Implementation Guidance;
Core Objectives 9: Stakeholder Communications;
Core Objectives 10: Software Update Information.
https://www.pcisecuritystandards.org/document_library
https://www.pcisecuritystandards.org/product-solutions-listings-overview